Kubernetes Series (Article 5): Rancher Deployment with Traefik, TLS (cert-manager), and Clean Auth
After completing my Kubernetes series [Article 4: Deploying Traefik Ingress and cert-manager in Kubernetes], I experimented with more exciting applications to run on my cluster. Initially, I considered installing Portainer, a popular container orchestration UI, but this time, I wanted to explore Rancher, one of the most powerful tools in the Kubernetes ecosystem.
Portainer and Rancher share some surface-level similarities: they provide a graphical interface to manage workloads, services, and resources inside Kubernetes. However, Rancher leaps ahead when simulating enterprise environments and managing multiple Kubernetes clusters. It’s far more capable, battle-tested, and extensible for full lifecycle Kubernetes management, covering everything from provisioning to RBAC, monitoring, GitOps, and multi-cluster upgrades.
Portainer, by contrast, shines in its simplicity. It’s ideal if you want a lightweight UI to manage containers and volumes, especially for learning, homelabs, or smaller projects. If you’re experimenting with container workloads or running a single-node K3S/K3d cluster, Portainer is a fantastic choice. But for anyone simulating real-world production setups, Rancher is better aligned with those goals.
In this article, I’ll walk through deploying Rancher on Kubernetes using Traefik as the Ingress Controller, backed by a TLS certificate issued via cert-manager, and secured using Rancher’s built-in authentication. My goal is to keep things clean, secure, and production-aligned.
IngressRoutes Instead of Kubernetes Ingress?
While Kubernetes-native Ingress resources work fine for basic routing, Traefik offers enhanced functionality through its custom resource definitions (CRDs) called IngressRoute. If you’re using Middlewares (e.g., for Basic Auth, IP whitelisting, or rate limiting), Traefik’s IngressRoute CRDs are much more flexible and robust.
For my setup, I wanted to:
- Serve Rancher securely at https://rancher.mydomain.com
- Use a custom TLS certificate issued by cert-manager
- Let Rancher handle authentication and access control internally, rather than configuring external Traefik Middlewares
This article covers everything from Helm-based Rancher deployment to exposing it behind a secure Traefik IngressRoute with clean TLS and authentication handling.
Stay tuned as I go step-by-step through setting up:
- A Traefik IngressRoute for Rancher
- Issuing a wildcard TLS cert using cert-manager
- Leveraging Rancher’s built-in authentication system for secure access
This setup works in homelabs and scales nicely for production-grade multi-cluster environments.
Stack Overview
| Component | Version / Notes |
|---|---|
| Rancher | v2.11.1 in High Availability mode (4 replicas) |
| Kubernetes | v1.30.13, provisioned using kubeadm |
| Ingress | Traefik with custom IngressRoute resources |
| TLS | cert-manager (with a Cloudflare DNS-01 ClusterIssuer) |
| Storage | Longhorn (installed, but not used by Rancher) |
Step 1: Install Rancher via Helm
Start by creating a Helm values file named rancher-values.yaml:
replicas: 4
resources:
requests:
cpu: 200m
memory: 512Mi
limits:
cpu: 2000m
memory: 1Gi
bootstrapPassword: YOUR_PASSWORDAdd the Rancher Helm repository and install the Rancher chart:
helm repo add rancher-latest https://releases.rancher.com/server-charts/latest
helm repo update
helm install rancher rancher-latest/rancher \
-n cattle-system \
--create-namespace \
-f rancher-values.yaml \
--set hostname=rancher.YOUR_DOMAIN.uk \
--set ingress.tls.source=noneAlready deployed Rancher? Use helm upgrade Instead:
helm upgrade rancher rancher-latest/rancher \
-n cattle-system \
-f rancher-values.yaml \
--set hostname=rancher.YOUR_DOMAIN.uk \
--set ingress.tls.source=noneStep 2: Define a Traefik IngressRoute for Rancher
Traefik replaces Rancher’s default ingress setup, offering better control and observability. Here’s a custom IngressRoute Definition:
apiVersion: traefik.io/v1alpha1
kind: IngressRoute
metadata:
name: rancher-ui
namespace: cattle-system
spec:
entryPoints:
- websecure
routes:
- match: Host(`rancher.YOUR_DOMAIN.uk`)
kind: Rule
services:
- name: rancher
namespace: cattle-system
port: 443
tls:
secretName: traefik-tlsThis setup does not use any middleware; Rancher handles authentication internally.
Step 3: Provision a TLS Certificate with cert-manager
Create a certificate resource to request a TLS certificate for your Rancher domain:
apiVersion: cert-manager.io/v1
kind: Certificate
metadata:
name: traefik-tls
namespace: cattle-system
spec:
secretName: traefik-tls
commonName: rancher.YOUR_DOMAIN.uk
dnsNames:
- rancher.YOUR_DOMAIN.uk
issuerRef:
name: cloudflare
kind: ClusterIssuer
duration: 2160h # 90 days
renewBefore: 168h # 7 daysApply the certificate manifest:
kubectl apply -f rancher-cert.yamlOnce validated, the TLS certificate will be stored in a Kubernetes secret called traefik-tls.
Step 4: Reset Admin Password (If Needed)
If the bootstrapPassword was not applied, or you can’t log in:
List the Rancher pods:
kubectl -n cattle-system get pods -l app=rancherExecute into a pod and reset the password:
kubectl -n cattle-system exec -it rancher-XXXX -- reset-passwordThis will output a username like user-xxxxx and a temporary password for logging in.
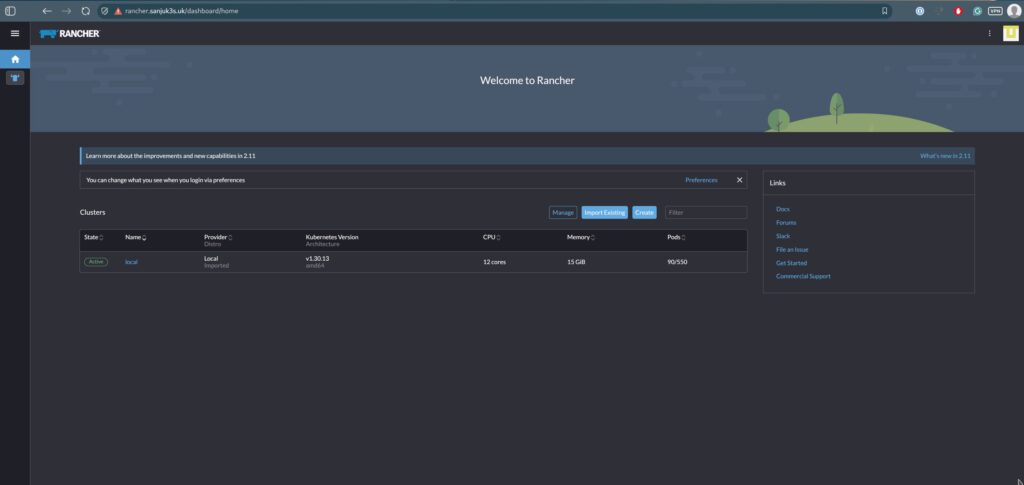
Step 5: Rancher Web UI Setup
Visit the Rancher web interface at:https://rancher.YOUR_DOMAIN.uk
Follow the setup wizard:
- Confirm the server URL.
- Log in using your admin credentials.
- Set a new password.
- Proceed to configure authentication providers or local users.
No Middleware?
Traefik’s middleware for Basic Auth or Forward Auth is not used here. Rancher provides robust built-in authentication options, including:
- Local user management
- GitHub / GitLab integration
- LDAP, Active Directory
- SAML-based SSO providers
Keeping authentication within Rancher ensures a clean, seamless login flow with audit trail and RBAC support.
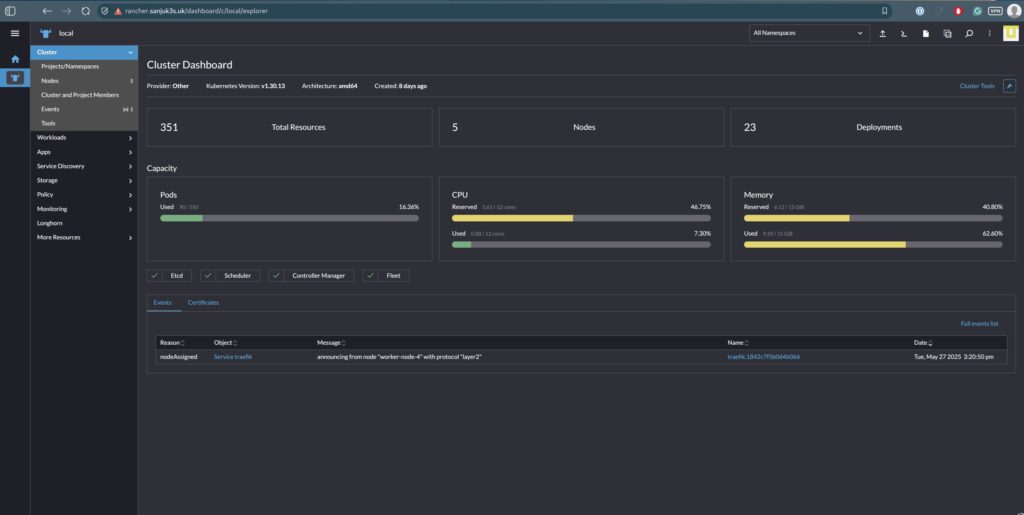
Final Architecture Snapshot
| Component | Status |
|---|---|
| Rancher | HA Mode (4 pods) |
| Ingress | Managed by Traefik with IngressRoute |
| TLS | Managed by cert-manager using Cloudflare DNS |
| Auth | Rancher-native authentication only |
| UI URL | https://rancher.YOUR_DOMAIN.uk |
Conclusion
With this setup, you now have:
- A highly available Rancher cluster
- Secured via automated TLS
- Exposed cleanly using Traefik
- Powered by Kubernetes, not locked into third-party auth proxies
This configuration is ideal for homelabs, testing environments, or production clusters where complete control and auditability are essential.