Proxmox, VLANs, QNAP Switch & pfSense:
In this write-up, I am exploring my home lab setup in depth. The document outlines the VLAN-aware setup used in a Proxmox-based home lab to securely and logically segment different types of traffic using a QNAP-managed switch and pfSense as the core firewall/router.
Proxmox Network Design:
I have configured my Proxmox with a single Linux bridge (vmbr0) using a 10GbE NIC, which is VLAN-aware. This allows for multiple VLANs to be managed without requiring separate physical interfaces.
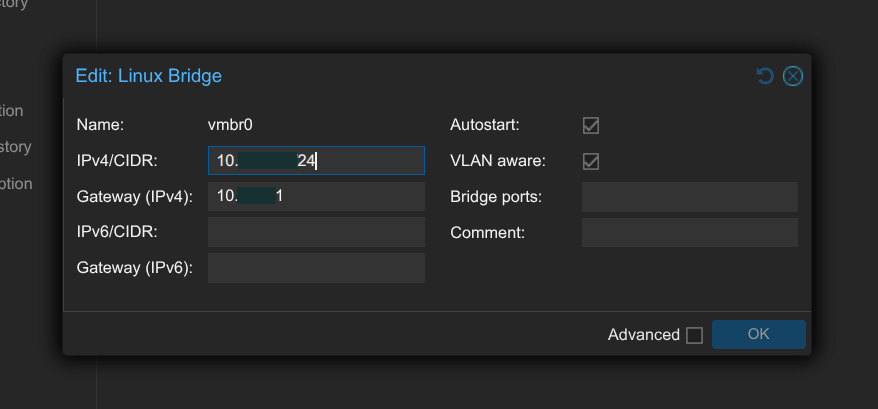
My /etc/network/interfaces File
auto lo
iface lo inet loopback
auto enp45f0
iface enp45f0 inet manual
auto vmbr0
iface vmbr0 inet static
address 10.x.x.x/24
gateway 10.x.x.1
bridge-ports enp45f0
bridge-stp off
bridge-fd 0
bridge-vlan-aware yes
bridge-vids 2-4094When I create a VM in Proxmox, I assign vmbr0 as the network interface and specify the VLAN ID (e.g., 80 for DMZ). This allows VMs to be placed on isolated subnets without additional bridge interfaces.
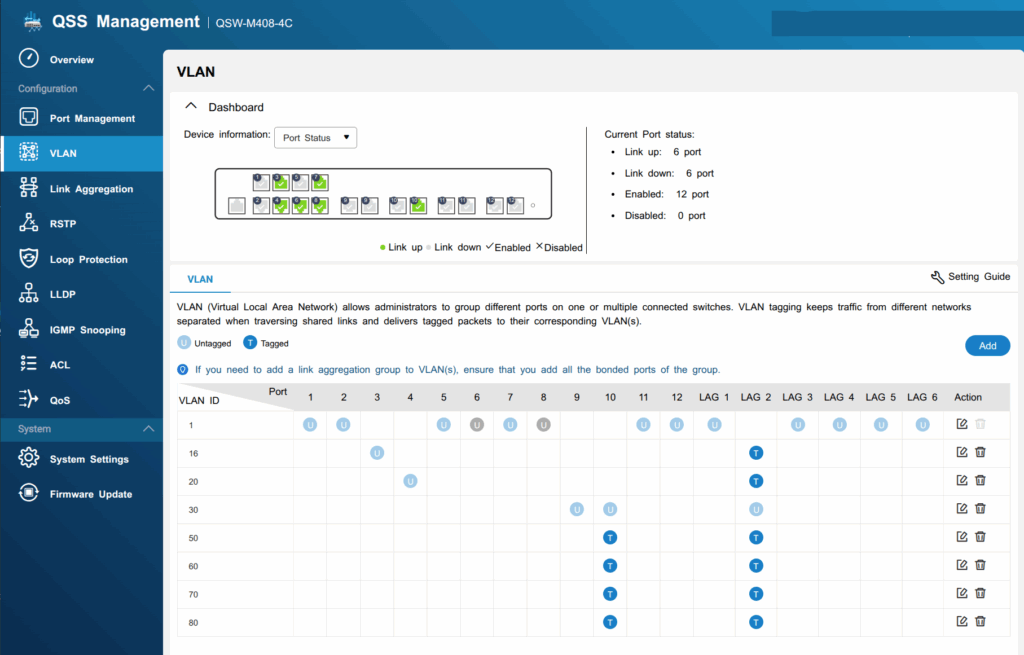
QNAP Managed Switch (QSW-M408-4C)
The following VLAN IDs are assigned across relevant ports:
General VLAN
VLAN 30 Example
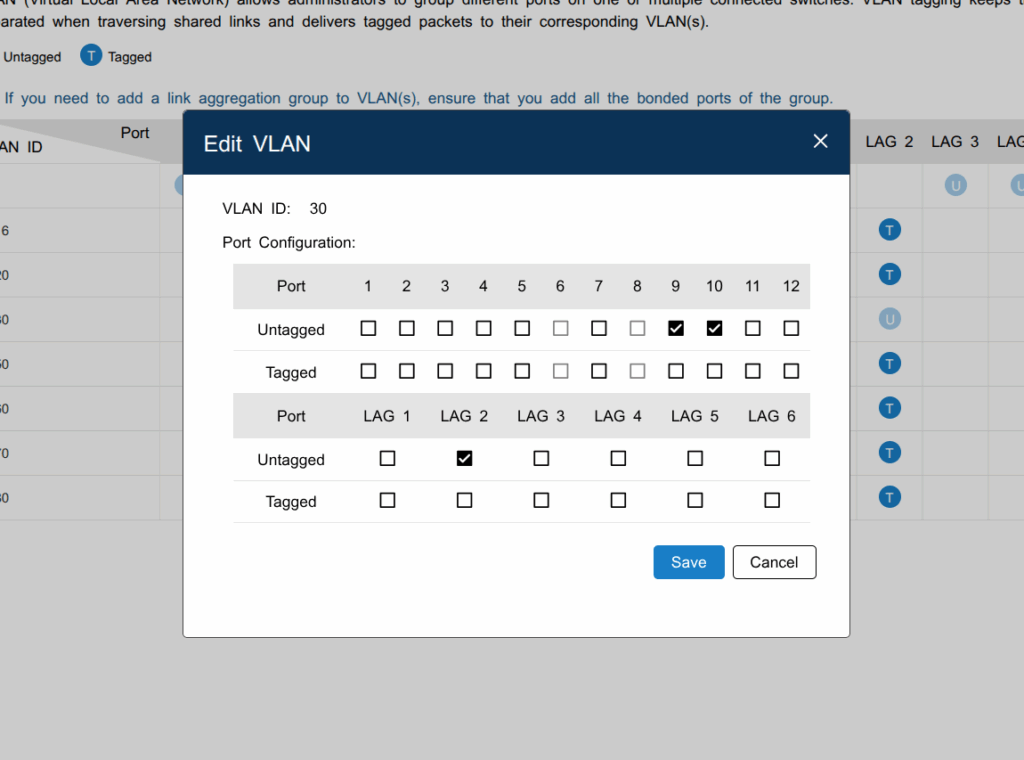
- Ports 9 & 10: Untagged (for Proxmox and workstation)
- LAG 2: Trunked/tagged for all VLANs (to pfSense)
Link Aggregation
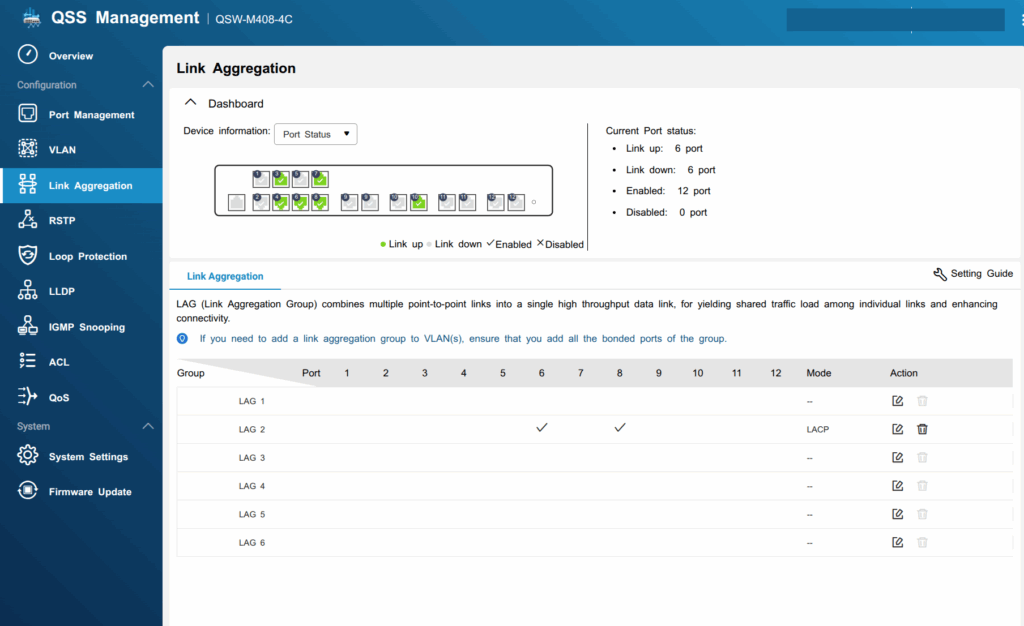
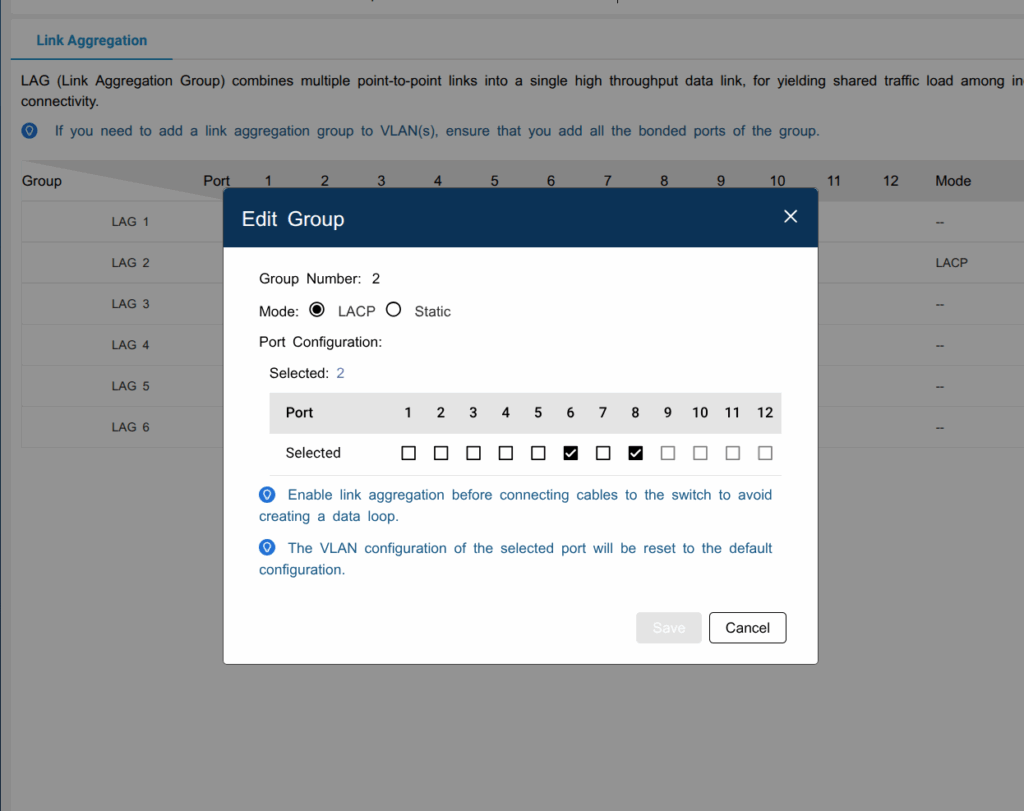
LAG 2 consists of ports 6 and 8 in LACP mode, connected to pfSense.
pfSense VLAN Assignments
Each VLAN has a corresponding interface in pfSense with firewall rules, DHCP, and routing configured.
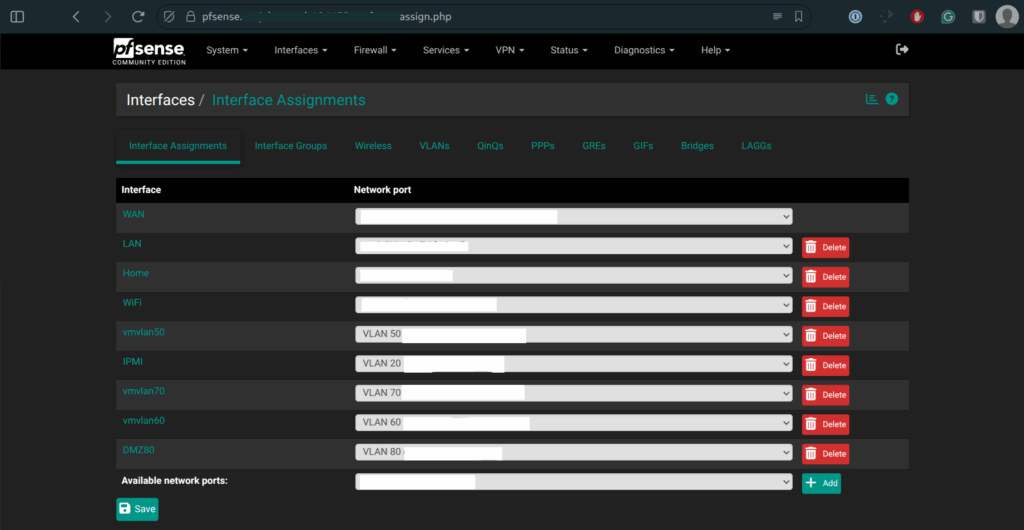
Each VLAN is isolated via firewall rules and optionally routed via NAT, depending on the need.
This architecture provides secure, isolated environments for:
- Proxmox management
- VM workloads (segmented by type/function)
- IPMI/BMC traffic
- Home and WiFi networks
- DMZ/public-facing services
This design uses a VLAN-aware bridge in Proxmox, tagged trunk uplinks to pfSense, and port-based VLAN configurations in a managed switch, enabling a powerful and flexible home lab environment.
One NIC for Proxmox
1. VLAN-Aware Bridge (vmbr0) Handles Multiple Networks
- My Proxmox uses a single bridge
vmbr0withbridge-vlan-aware yes. - All VLANs are managed virtually by tagging traffic per VM.
- No need for physical separation if the switch and firewall (pfSense) are handling VLAN isolation.
2. Switch Tagging + pfSense Routing = Full Control
- My QNAP switch tags traffic correctly.
- pfSense routes and isolates VLANs via firewall rules.
- So one NIC handles many networks securely.
3. 10GbE Bandwidth Is Plenty
- 10GbE has more than enough throughput for multiple VMs, backups, etc.
- I want to avoid complexity and cabling clutter while gaining performance.
Best Practices for Single-NIC Setups
| Topic | Recommendation |
|---|---|
| VLAN Tagging | Use per-VM VLAN IDs via vmbr0 |
| Uplink to Switch | Tagged trunk port (like my LAG setup) |
| pfSense VLAN Interfaces | One per VLAN, each with its own rules/DHCP |
| Backups or Storage | One per VLAN, each with its rules/DHCP |
